
Having had a very busy back to my regular job as a DevOps consultant as well completing my presentation slides, it was time for some much needed time away with my good lady. We stayed in a local hotel and thoroughly enjoyed our time together – away from the distractions of work and studies it was lovely to have a nice time together – and did I sleep well !
I returned to work and then my studies in the evening, with the added bonus that the near-field antennas I had ordered from Ebay had arrived !
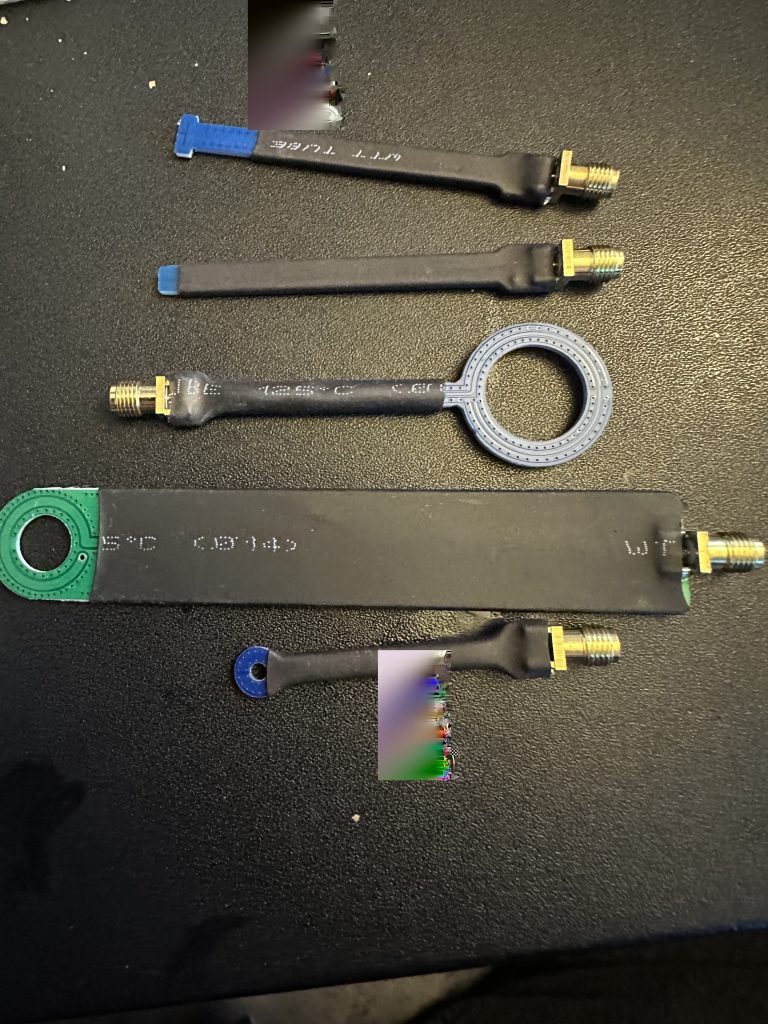
I’m always a little dubious of ordering goods from Ebay, they can look great in the pictures and never sure they can actually work. In the first instance I tried it with my Raspberry Pi4, and didn’t detect any signals on the clock frequency of the processor (600Mhz), I was able to confirm the log frequency using the following command.
cat /sys/devices/system/cpu/cpu0/cpufreq/scaling_cur_freq
600000So I should be picking up something at 600Mhz, but to no avail.

I continued to strip down the RPi4, removing the heat sink, the casing, but no results. I reviewed the academic paper (Sayakkara,2019) and noticed that a RPi3b was being used, and the processor shielding was different. With that I went thru my pile of technology projects and used my NOAA receiver which wasn’t currently in use, but a RPi3b board. I re-loaded Debian buster on a new flash card (keeping the NOAA one safe, its alot of configuration to get it working…) and tried the near field antenna once more.
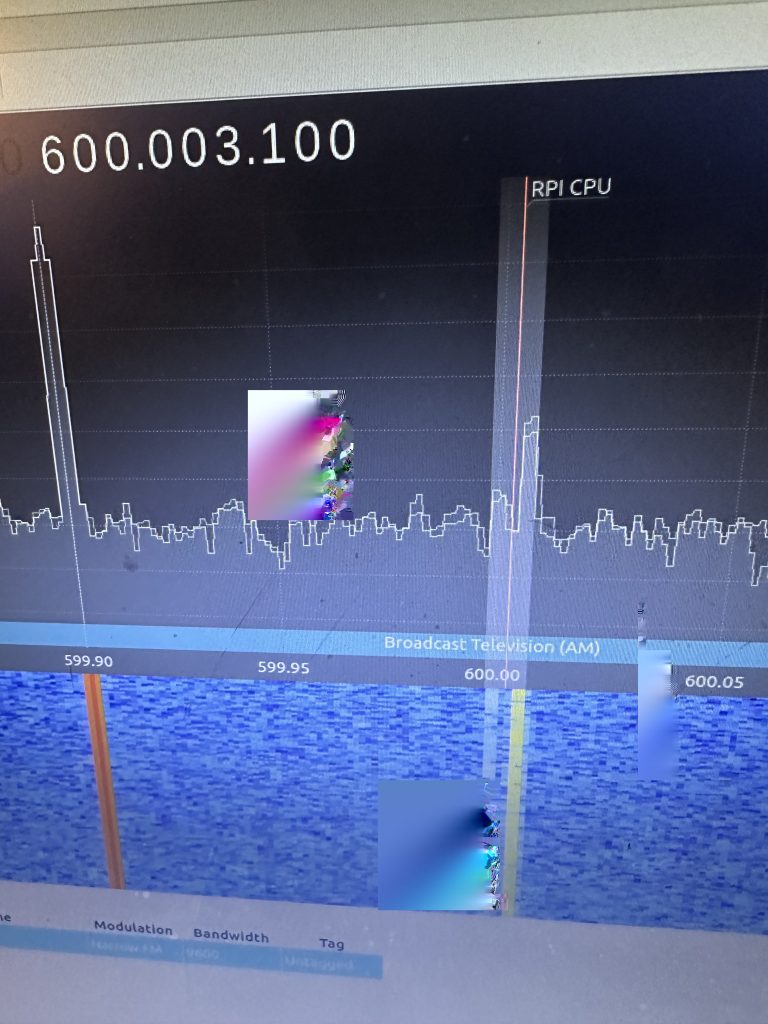

Sure enough I was picking up signals right away and could prove by moving the antenna around it was the CPU I was monitoring. I’ve used a jar to hold the antenna in place for now, but have ordered a better solution by way of a ‘helping hands’ setup, which will allow the antenna to be placed at the best distance to get spurious signals from the CPU to the HackRF.
I’ve found the gitlab repo which contains all the code which was used to conduct the experiments, so my next step is to re-create those given in the paper and compare my results, then I can start investigating coding in other languages.
Hopefully next weeks post (planning once per week on a Sunday) will demonstrate the capture.machine learning and cryptanalysis of the various ciphers (3DES, AES, RSA).